I. System Overview <br> <br> With the rapid development of China's economy, especially in the major areas of crime have occurred for the financial sector, bank vault every day involve large amounts of cash out of storage work. The scope of work of armored cars also covers places such as vaults, physical outlets, and self-service banks. Therefore, it is easy to become a target of financial crimes. Since the contracting system of escort work, banks will put forward higher requirements for the safety of escort trucks and escort personnel. The Chinese Ministry of Public Security, the People’s Bank of China, and the China Banking Regulatory Commission repeatedly issued administrative documents to emphasize repeatedly the requirement to establish and establish the internal control system of the entire financial industry escort to prevent the use of counterfeit escort trucks and counterfeit escorts for criminal activities, and requested that Enhance the ability to prevent escort work risks by improving technical certification. In May 2001, Wenzhou Bank of China's counterfeit armored car took advantage of a security loophole in the exchange of money received by the bank's supervision center to take away huge amounts of cash; in early 2006, a certain bank escort in Shenyang used the authority and management loopholes and transferred more than 300 funds. Ten thousand yuan and fled. It has been wanted by authorities. These facts indicate that current bank escort management needs more scientific and safe management tools. This system is aimed at a set of escort personnel identity authentication systems designed to prevent false identification of personnel and update information in the process of bank escort in recent years. This system adopts a mature automatic identification technology for living fingerprints. It is certified to humans and RFID Bluetooth card reader technology is certified to escort trucks and boxes. At the same time, it uses the Internet to update the escort schedules and personnel data in real time to ensure the accuracy of the authentication during the handover. , Exclude the possibility of private transfer, and during the verification process, the language broadcaster's name, display person's name, photo comparison, etc., to strengthen the management, eliminate the occurrence of crime such as impersonation, and provide accurate and timely certification records. The system uses the network and the identification terminal to save the expenses of the deployment system to the utmost extent and ensure the security of the system. The transport of banknotes is a key part of the bank's safe operation, and it is related to the normal operation of bank outlets and the safety of funds. The cash transfer area is usually in the cash area of ​​the bank outlets. The cash area is the core area for bank outlets' security. The cash area linkage gate is the "door of the employee's life," and only qualified personnel can enter the cash area. In addition, with the vigorous promotion of escort outsourcing, the outsourcing rate for financial escort is now over 96%, while outsourced service personnel and cash transport service vehicles are often random and highly mobile. It is only by relying on traditional manual comparison of license plates and photos. Can not effectively and effectively implement the identity verification work of the transfer of money transfer link. The Bank conducted several investigations and inspections and found that some lines exist problems such as lack of identity authentication, irregularity, and formality, which brings certain hidden troubles to the transfer of money transfer notes. Therefore, the bank urgently needs to strengthen the authentication of the money transfer process. Through the use of an electronic identity authentication system, it can effectively identify the transport vehicles and transfer personnel, and improve the safety of money transfer.
Second, system function and system flow
1. System function introduction 1) Vehicle certification According to the escort plan, the escort business personnel arrives at the designated area of ​​the bank with the cashier in the business network. At this time, the smart escort engine at the outlet sends the escort truck to the voice prompt outlet management personnel, and the escort truck arrives. The intelligent escort host display on the screen displays the photos of the escort personnel and the occupants of the vehicle and the personnel information. The management personnel can directly identify the vehicle and the detaining personnel.
2) After the escort person's identity verification and face grab comparison are completed, the escort personnel will perform fingerprint authentication on the smart escort extension at the linkage door, and at the same time capture the facial photos of the certification personnel through the camera on the extension. Once the verification passes, The system automatically displays the authenticated escort personnel information and captured facial photos on the smart escort host display screen. The management personnel can easily compare the original storage photos of the escort personnel with face photographs captured in real time. The system carries out the dual authentication function of automatic fingerprint biometric identification and artificial photo comparison to realize joint control and joint control, and to achieve the combination of physical defense and technical prevention.
3) Business Commissioner Identity Authentication When the escort vehicle, escort personnel, and cash box certification are completed, the bank sales representative needs to perform fingerprint identification to confirm that the transaction is successful, the smart escort host displays a photo of the business commissioner to determine, and the voice broadcast: “Business The Commissioner xxx is certified to be successful. At the same time, the authentication information is automatically transmitted to the management center for storage, and the central server voice broadcast prompts to realize the responsibility to the people.
4) The schedule management center vault can schedule the debit schedule every day, select the corresponding “debit banknotes, debit notes, outlets, debit notes, and receipt information†and deliver the handover task to the network point intelligent escort host.
5) Handover process Packing personnel certification, vehicle certification, cash box certification, salesperson fingerprint confirmation information packaged into a message upload center, (with the entire handover process as a package), the monitoring center received similar e-mail information, such as the need to understand the entire handover details Information, double-click to open the package 6) Transfer of money box According to the escort plan, the escort business personnel first go to the vault (or business outlets) handover area to complete the personnel certification, and the vault (or outlet) management personnel open the isolation door and the debit keeper in the vault (or outlet ) The transfer area starts the transfer of the cash box. At this time, the system automatically identifies the number of the transfer box and the number of the cash box, generates a transfer report, prints the transfer report directly through the printing device, and deposits money with the vault (or outlet). Trace, confirm handover completed.
7) Illegal authentication alarm:
When someone authenticates the fingerprint five times in a row, the system automatically restarts the task and sends an authentication error alarm message to the management center.
8) Case wrong box alarm:
When the debenture holder raised the wrong money box, the money box belonging to the A network point was sent to the B network point, and the system automatically reported an alarm.
9) Lost alarm:
When the number of moneyboxes sent to the bank and the number of dispatched plans cannot be matched, the system will automatically call the police.
10) Banknote jumping alarm:
When the cash car is not handed over according to the established line, the system will automatically alarm.
11) Personnel Information Import Personnel information can be collected from the personnel collection system of the escort company and imported into the central software in an encrypted file format, thus avoiding the network restrictions of the bank and the escort company and collecting troubles.
12) Risk handling The handover process is normally normal and there is no need to alert the software. When there is something wrong with the handover process, risk management and software alerts should be started.
13) Importing of disconnected network tasks When problems occur in the banking network, the system can download tasks by encrypting the mobile terminal. After the network reaches the network, the system performs interception work after the import task is performed on the authentication front-end machine.
14) Fingerprint Management:
Fingerprints can be collected in various ways such as central collection and front-end dot collection.
15) Intelligent voice human-computer interaction:
Throughout the entire handover process, voice and graphic prompts and announcements are made. The outlets display operations based on voice prompts and graphic texts, making the use process simple and convenient.
16) Central software TTS voice prompts:
When there is a handover record or an alarm event, the central server automatically broadcasts voice reports to remind the on-duty personnel to handle the operation.
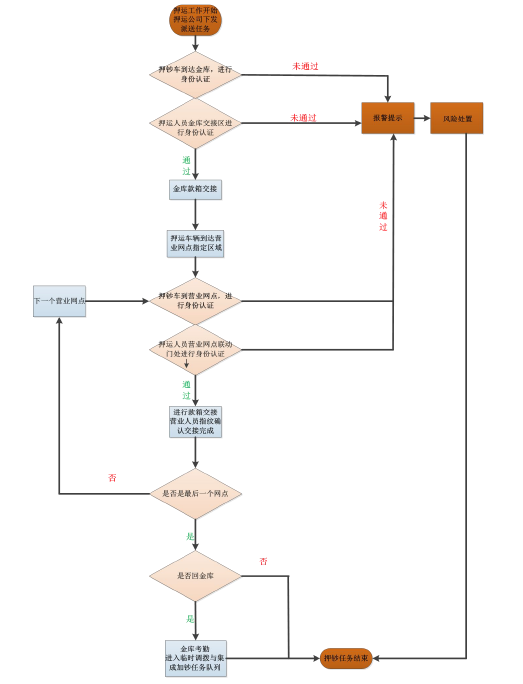
2. System Workflow 1) Delivery process The escort company dispatches tasks and issues the task. The escort truck arrives at the central vault, the escort personnel conduct identity verification, the central vault performs the transfer of the purse, the escort vehicle departs to the delivery network, and the network voice prompts. When the teller arrives, the detainer arrives at the linkage door to perform identity verification. After the success, the business outlet opens the linkage door. After the demobilization personnel arrive at the network handover area, the system performs the identification of the receipt box. After the completion of the handover, the business network staff will confirm the handover and transfer the connection. The work is completed. The punt car goes to the next outlet.
2) Recycling money box process The company's arranging task of repatriating money box and issuing the task shall be issued. The money teller will start to arrive at the designated outlets. The network will voice the reminder to the arrival of the telling machine. The demobilization personnel will arrive at the linkage door to perform the authentication. After the success, the business outlet will open. After the linkage door was opened and the demobilization personnel arrived at the network handover area, after the handover was completed, staff at the business outlets confirmed the handover and completed the handover. The remand car was returned to the central treasury, and the vault reminded that the pledger arrived and the detaining staff had to verify their identity. After the success, the detainees arrive at the handover area and the system automatically conducts the identification of the case. After the transfer is completed, the vault staff confirms the handover and the handover is completed.
3) Temporary transfer or central banknote increase tasks The task of temporary transfer or central banknote increase is the same as above.
3. Diagram of the electronic identity authentication system for escorts (vehicles and cases)
Second, system function and system flow
1. System function introduction 1) Vehicle certification According to the escort plan, the escort business personnel arrives at the designated area of ​​the bank with the cashier in the business network. At this time, the smart escort engine at the outlet sends the escort truck to the voice prompt outlet management personnel, and the escort truck arrives. The intelligent escort host display on the screen displays the photos of the escort personnel and the occupants of the vehicle and the personnel information. The management personnel can directly identify the vehicle and the detaining personnel.

2) After the escort person's identity verification and face grab comparison are completed, the escort personnel will perform fingerprint authentication on the smart escort extension at the linkage door, and at the same time capture the facial photos of the certification personnel through the camera on the extension. Once the verification passes, The system automatically displays the authenticated escort personnel information and captured facial photos on the smart escort host display screen. The management personnel can easily compare the original storage photos of the escort personnel with face photographs captured in real time. The system carries out the dual authentication function of automatic fingerprint biometric identification and artificial photo comparison to realize joint control and joint control, and to achieve the combination of physical defense and technical prevention.

3) Business Commissioner Identity Authentication When the escort vehicle, escort personnel, and cash box certification are completed, the bank sales representative needs to perform fingerprint identification to confirm that the transaction is successful, the smart escort host displays a photo of the business commissioner to determine, and the voice broadcast: “Business The Commissioner xxx is certified to be successful. At the same time, the authentication information is automatically transmitted to the management center for storage, and the central server voice broadcast prompts to realize the responsibility to the people.

4) The schedule management center vault can schedule the debit schedule every day, select the corresponding “debit banknotes, debit notes, outlets, debit notes, and receipt information†and deliver the handover task to the network point intelligent escort host.
5) Handover process Packing personnel certification, vehicle certification, cash box certification, salesperson fingerprint confirmation information packaged into a message upload center, (with the entire handover process as a package), the monitoring center received similar e-mail information, such as the need to understand the entire handover details Information, double-click to open the package 6) Transfer of money box According to the escort plan, the escort business personnel first go to the vault (or business outlets) handover area to complete the personnel certification, and the vault (or outlet) management personnel open the isolation door and the debit keeper in the vault (or outlet ) The transfer area starts the transfer of the cash box. At this time, the system automatically identifies the number of the transfer box and the number of the cash box, generates a transfer report, prints the transfer report directly through the printing device, and deposits money with the vault (or outlet). Trace, confirm handover completed.
7) Illegal authentication alarm:
When someone authenticates the fingerprint five times in a row, the system automatically restarts the task and sends an authentication error alarm message to the management center.
8) Case wrong box alarm:
When the debenture holder raised the wrong money box, the money box belonging to the A network point was sent to the B network point, and the system automatically reported an alarm.
9) Lost alarm:
When the number of moneyboxes sent to the bank and the number of dispatched plans cannot be matched, the system will automatically call the police.
10) Banknote jumping alarm:
When the cash car is not handed over according to the established line, the system will automatically alarm.
11) Personnel Information Import Personnel information can be collected from the personnel collection system of the escort company and imported into the central software in an encrypted file format, thus avoiding the network restrictions of the bank and the escort company and collecting troubles.
12) Risk handling The handover process is normally normal and there is no need to alert the software. When there is something wrong with the handover process, risk management and software alerts should be started.
13) Importing of disconnected network tasks When problems occur in the banking network, the system can download tasks by encrypting the mobile terminal. After the network reaches the network, the system performs interception work after the import task is performed on the authentication front-end machine.
14) Fingerprint Management:
Fingerprints can be collected in various ways such as central collection and front-end dot collection.
15) Intelligent voice human-computer interaction:
Throughout the entire handover process, voice and graphic prompts and announcements are made. The outlets display operations based on voice prompts and graphic texts, making the use process simple and convenient.
16) Central software TTS voice prompts:
When there is a handover record or an alarm event, the central server automatically broadcasts voice reports to remind the on-duty personnel to handle the operation.
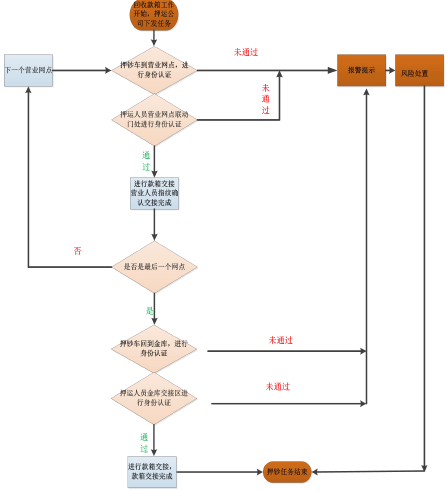
2. System Workflow 1) Delivery process The escort company dispatches tasks and issues the task. The escort truck arrives at the central vault, the escort personnel conduct identity verification, the central vault performs the transfer of the purse, the escort vehicle departs to the delivery network, and the network voice prompts. When the teller arrives, the detainer arrives at the linkage door to perform identity verification. After the success, the business outlet opens the linkage door. After the demobilization personnel arrive at the network handover area, the system performs the identification of the receipt box. After the completion of the handover, the business network staff will confirm the handover and transfer the connection. The work is completed. The punt car goes to the next outlet.
2) Recycling money box process The company's arranging task of repatriating money box and issuing the task shall be issued. The money teller will start to arrive at the designated outlets. The network will voice the reminder to the arrival of the telling machine. The demobilization personnel will arrive at the linkage door to perform the authentication. After the success, the business outlet will open. After the linkage door was opened and the demobilization personnel arrived at the network handover area, after the handover was completed, staff at the business outlets confirmed the handover and completed the handover. The remand car was returned to the central treasury, and the vault reminded that the pledger arrived and the detaining staff had to verify their identity. After the success, the detainees arrive at the handover area and the system automatically conducts the identification of the case. After the transfer is completed, the vault staff confirms the handover and the handover is completed.
3) Temporary transfer or central banknote increase tasks The task of temporary transfer or central banknote increase is the same as above.
3. Diagram of the electronic identity authentication system for escorts (vehicles and cases)
Aerosol Cone & Dome Production Line
Aerosol Cone & Dome Production Line,Automatic Aerosol Cone & Dome Production Line,Aerosol Cone & Dome Making Line,Aerosol Can Cone Dome Making Machine
Zhejiang Golden Eagle Food Machinery Co.,Ltd. , https://www.goldeneaglecanmaking.com